Diving into RFID Protocols with Flipper Zero使用 Flipper Zero 深入研究 RFID 协议
RFID is a contactless radio-tag technology. It is quite common and you may see it in a lot of places: intercoms, bank cards, public transport passes, office passes, they are used to track domestic animals, for toll collection, etc. The two main RFID tag types are high frequency and low frequency.
RFID 是一种非接触式无线电标签技术。它很常见,你可能会在很多地方看到它:对讲机、银行卡、公共交通通行证、办公室通行证,它们用于跟踪家畜、收费等。两种主要的 RFID 标签类型是高频和低频。
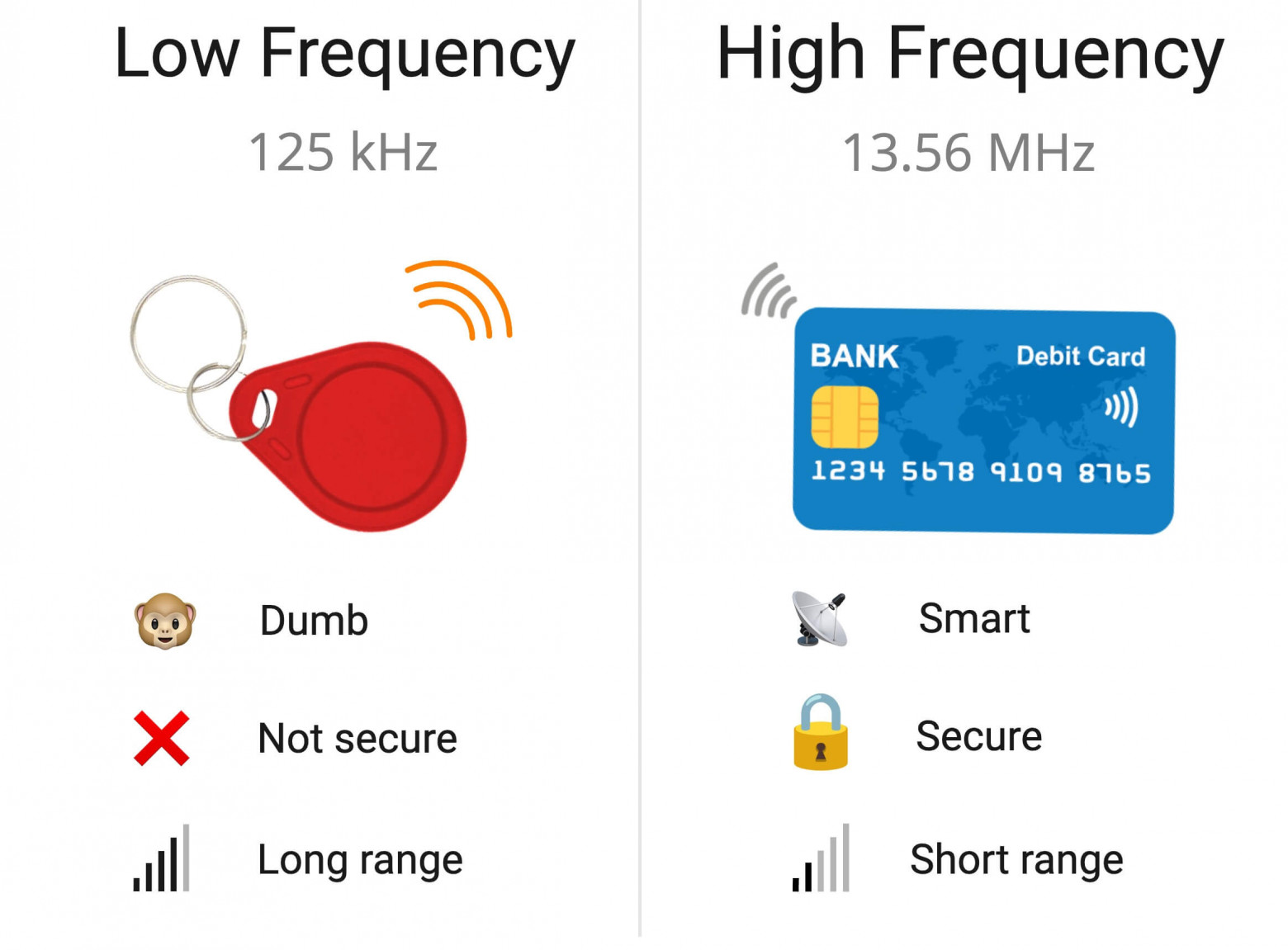
- Low-Frequency tags (125 kHz) — work at a higher range. Despite being insecure and dumb, they are still used in primitive access control systems: in building intercoms, offices, sports facilities, museums.
低频标签(125 kHz) — 在更高的范围内工作。尽管不安全且愚蠢,它们仍然用于原始的访问控制系统:楼宇对讲、办公室、体育设施、博物馆。 - High-Frequency tags (13.56 MHz) — have a lower effective range when compared with the low-frequency ones but have more complex protocols. They support encryption, authentication, and cryptography. These tags are commonly used in contactless bank cards, to pay for public transport, and in high-security access control systems.
高频标签(13.56 MHz) — 与低频标签相比,有效范围较低,但协议更复杂。它们支持加密、身份验证和密码学。这些标签通常用于非接触式银行卡、公共交通支付以及高安全性门禁系统。
Here we will compare these two types of tags, take a look at the main protocols and learn to work with them using Flipper Zero — we will read, emulate, save and clone them. You will see how you will be able to save your office, sports, home whatever RFID keys you have and we'll take a glimpse at what Flipper can read from a bank card.
在这里,我们将比较这两种类型的标签,查看主要协议并学习使用 Flipper Zero 来使用它们——我们将读取、模拟、保存和克隆它们。您将看到如何能够保存您的办公室、运动、家庭中的任何 RFID 钥匙,我们将了解 Flipper 可以从银行卡中读取什么。
How RFID Tags Work RFID 标签的工作原理

RFID 芯片在接收到来自阅读器 RF 场的电源时开启
Most RFID tags are passive tags with no internal power source. The chip inside is completely turned off until the tag is exposed to a reader's electromagnetic field. As soon as it comes within range, the tag's antenna begins absorbing energy from the reader's EM field and the chip receives power. The chip then turns on and begins communicating with the reader. It's worth mentioning, that a tag's antenna is tuned to a specific frequency, so the tag can only activate when it is inside a suitable electromagnetic field.
大多数 RFID 标签都是无源标签,没有内部电源。内部芯片完全关闭,直到标签暴露在阅读器的电磁场中。一旦进入范围,标签的天线就开始从阅读器的电磁场吸收能量,并且芯片接收电力。然后芯片打开并开始与读卡器通信。值得一提的是,标签的天线被调谐到特定频率,因此标签只有在合适的电磁场内才能激活。
RFID Tag Types RFID 标签类型
On the outside RFID tags can be quite different: cards both fat or thin, key fobs, bracelets, coins, rings, or even stickers. Judging by the visuals alone it's almost impossible to distinguish the frequency or protocol the tag operates on.
从外部看,RFID 标签可能有很大不同:厚卡或薄卡、钥匙扣、手镯、硬币、戒指,甚至贴纸。仅从视觉效果来看,几乎不可能区分标签运行的频率或协议。

从外面看,RFID 标签可能有很大不同
Quite often manufacturers use similar plastic cases for different types of RFID fobs operating on different frequencies. Two absolutely visually similar tags might be totally different inside. It is worth considering when you try to distinguish the type of tag you have. In this article, we will be looking at the two most popular types of RFID tags that are used in access control systems. Flipper Zero supports both their frequencies.
制造商经常使用类似的塑料外壳来容纳在不同频率上运行的不同类型的 RFID 遥控钥匙。两个视觉上绝对相似的标签内部可能完全不同。当您尝试区分您拥有的标签类型时,值得考虑。在本文中,我们将了解访问控制系统中使用的两种最流行的 RFID 标签类型。 Flipper Zero 支持这两种频率。
There is a variety of RFID protocols working on other frequencies. UHF for example uses the 840-960 MHz range. They are used for tracking assets in warehouses, paying for toll roads, tracking wild animals during their migration and so forth. These tags may have a battery and work from a couple of meters to kilometers. They are quite rare though, and you may not encounter them unless you go looking for them specifically. We will omit them entirely for the purpose of this article.有多种在其他频率上工作的 RFID 协议。例如,UHF 使用 840-960 MHz 范围。它们用于跟踪仓库中的资产、支付收费公路费用、跟踪野生动物的迁徙等等。这些标签可能配有电池,工作范围可达几米到几公里。不过它们非常罕见,除非你专门去找它们,否则你可能不会遇到它们。为了本文的目的,我们将完全省略它们。
125 kHz & 13.56 MHz – Which is Which?
125 kHz 和 13.56 MHz – 哪个是哪个?
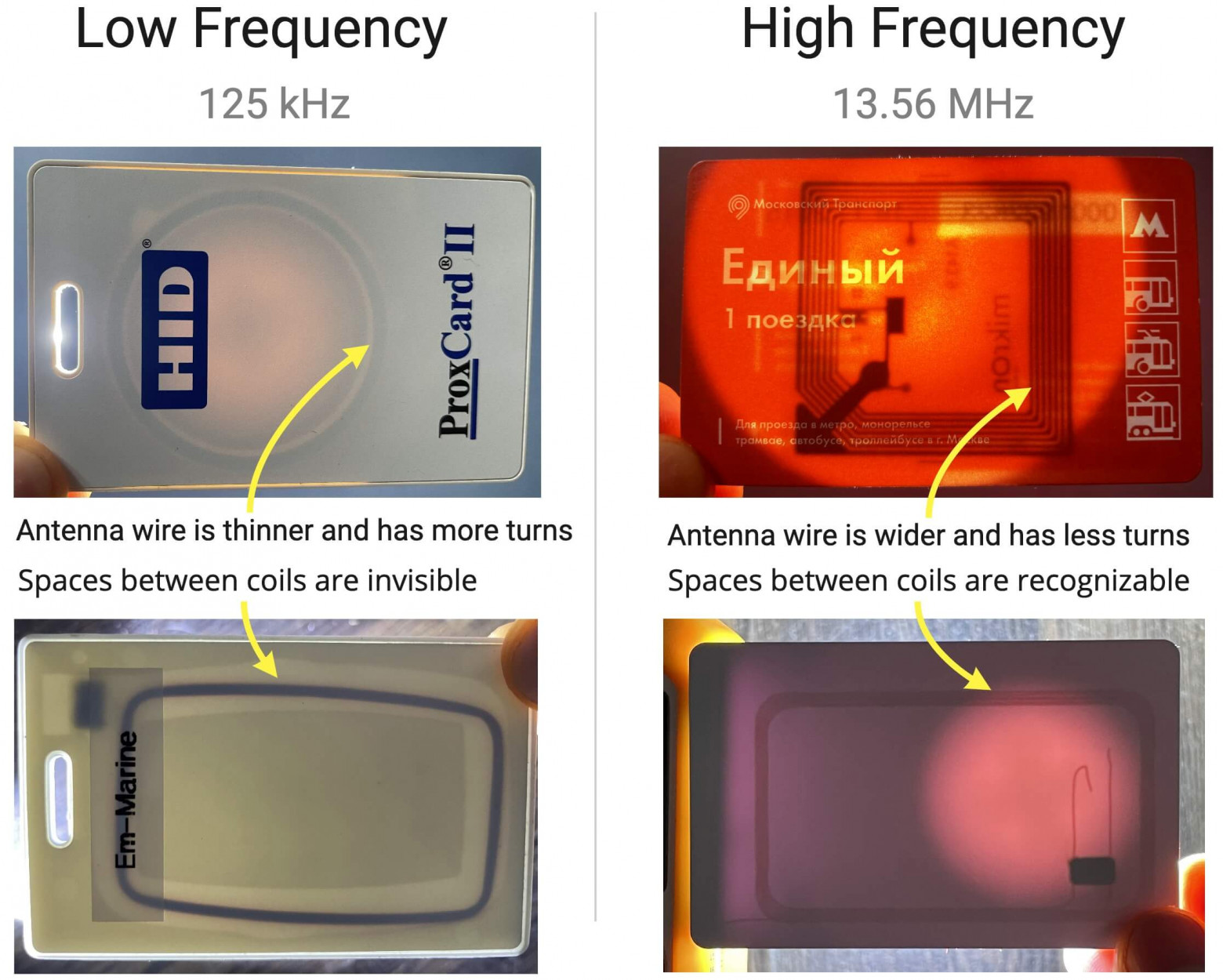
The easiest way to understand what range of the RFID tag is operating on is to look at the antenna. Low-frequency tags (125 kHz) have an antenna made of a very thin wire, literally thinner than a hair. But such antennas have a large number of turns, therefore, such an antenna looks like a solid piece of metal. High-frequency cards (13.56 MHz) have a significantly smaller number of thicker turns, with visible gaps between them.
了解 RFID 标签工作范围的最简单方法是查看天线。低频标签(125 kHz)的天线由非常细的电线制成,实际上比头发还细。但这种天线的匝数很多,因此,这种天线看起来就像一块坚固的金属。高频卡 (13.56 MHz) 的粗匝数量明显较少,且匝之间有明显的间隙。
在背光足够的情况下,可以猜测卡的工作频率
You can shine some light through an RFID card to see an antenna inside. If the antenna has only a few large turns, it is most likely a high-frequency antenna. If the antenna looks like a solid piece of metal with no gaps between the turns, it is a low-frequency antenna.
您可以通过 RFID 卡照射一些光来看到里面的天线。如果天线只有几个大匝,则很可能是高频天线。如果天线看起来像一块实心金属,匝之间没有间隙,那么它就是低频天线。

低频天线的匝数为细线,而高频天线则使用较粗的线
Low-frequency tags are often used in systems that do not require high security: building access, intercom keys, gym membership cards, etc. Due to their higher range, they are convenient to use for paid car parking: the driver does not need to bring the card close to the reader, as it is triggered from further away. At the same time, low-frequency tags are very primitive, they have a low data transfer rate. For that reason, it's impossible to implement complex two-way data transfer for such things as keeping balance and cryptography. Low-frequency tags only transmit their short ID without any means of authentication.
低频标签常用于安全性要求不高的系统中:楼宇门禁、对讲钥匙、健身房会员卡等。由于其范围较高,因此方便用于付费停车场:驾驶员无需将卡靠近读卡器,因为它是从较远的地方触发的。同时,低频标签非常原始,它们的数据传输率较低。因此,不可能实现复杂的双向数据传输,例如保持平衡和加密。低频标签仅传输其短ID,而没有任何身份验证手段。
High-frequency tags are used for a more complex reader-tag interaction when you need cryptography, a large two-way data transfer, authentication, etc.
当您需要加密、大量双向数据传输、身份验证等时,高频标签可用于更复杂的阅读器与标签交互。
It's usually found in bank cards, public transport, and other secure passes.
它通常存在于银行卡、公共交通和其他安全通行证中。
125 kHz 和 13.56 MHz RFID 标签比较
Low-Frequency 125 kHz Tags
低频 125 kHz 标签
- Long Range — lower frequency translates to higher range. There are some EM-Marin and HID readers, which work from a distance of up to a meter. These are often used in car parking.
长距离— 较低的频率可转化为较高的范围。有一些 EM-Marin 和 HID 读卡器,工作距离可达一米。这些通常用于停车场。 - Primitive protocol — due to the low data transfer rate these tags can only transmit their short ID. In most cases, data is not authenticated and it's not protected in any way. As soon as the card is in the range of the reader it just starts transmitting its ID.
原始协议——由于数据传输速率低,这些标签只能传输它们的短 ID。在大多数情况下,数据未经身份验证,也不受任何方式的保护。一旦卡处于读卡器的范围内,它就会开始传输其 ID。 - Low security — These cards can be easily copied, or even read from somebody else's pocket due to the protocol's primitiveness.
安全性低——由于协议的原始性,这些卡很容易被复制,甚至可以从别人的口袋里读取。
High-Frequency 13.56 MHz Tags
高频 13.56 MHz 标签
- Low range — high-frequency cards are specifically designed so that they would have to be placed close to the reader. This also helps to protect the card from unauthorized interactions. The maximum read range that we managed to achieve was about 15 cm, and that was with custom-made high-range readers.
低范围-高频卡经过专门设计,因此必须放置在靠近读卡器的位置。这也有助于保护卡免遭未经授权的交互。我们成功实现的最大读取范围约为 15 厘米,这是使用定制的高范围读取器实现的。 - Advanced protocols — data transfer speeds up to 424 kbps allow complex protocols with full-fledged two-way data transfer. Which in turn allows cryptography, data transfer, etc.
高级协议— 数据传输速度高达 424 kbps,支持复杂的协议和成熟的双向数据传输。这反过来又允许加密、数据传输等。 - High security — high-frequency contactless cards are in no way inferior to smart cards. There are cards that support cryptographically strong algorithms like AES and implement asymmetrical cryptography.
高安全性——高频非接触式卡丝毫不逊色于智能卡。有些卡支持 AES 等加密强度较高的算法,并实现非对称加密。
RFID in Flipper Zero Flipper Zero 中的 RFID

Flipper Zero 中的 RFID 天线如何工作
Flipper supports both high-frequency and low-frequency tags. To support both frequencies we developed a dual-band RFID antenna that is situated on the bottom part of the device.
Flipper 同时支持高频和低频标签。为了支持这两个频率,我们开发了位于设备底部的双频 RFID 天线。
A separate NFC controller (ST25R3916) is used for high-frequency protocols (NFC). It takes care of everything related to hardware interaction with the cards: reading and emulation. Low-frequency 125 kHz protocols are implemented programmatically via a custom analog frontend, that works in cooperation with MCU and also allows to read, write and emulate.
单独的 NFC 控制器 (ST25R3916) 用于高频协议 (NFC)。它负责与卡的硬件交互相关的所有事务:读取和仿真。低频 125 kHz 协议通过自定义模拟前端以编程方式实现,该前端与 MCU 配合工作,还允许读取、写入和仿真。[Video] RFID antenna inside Flipper Zero
[视频] Flipper Zero 内的 RFID 天线
The top part of the PCB is shielded with a ferromagnetic layer which isolates the rest of the electronic components from interference and extends the operating range by reflecting the high-frequency field.
PCB 的顶部采用铁磁层屏蔽,可隔离其余电子元件免受干扰,并通过反射高频场来扩展工作范围。
During assembly, the antennas are glued into Flipper's back panel. It connects to the PCB with pogo-pins. This greatly simplifies the assembly, as no cables are used and no UFL connectors are required.
在组装过程中,天线被粘在 Flipper 的背板上。它通过弹簧针连接到 PCB。这极大地简化了组装,因为不使用电缆,也不需要 UFL 连接器。
Low-Frequency 125 kHz Protocols
低频 125 kHz 协议
Low-frequency tags store a short ID, just a couple bytes long. The tag's ID is compared to IDs stored in the database of a controller or an intercom. However, the card will transmit its ID to anyone asking as soon as it receives power. Quite often the ID is inscribed on the card itself, so you can take a picture and input it into the Flipper manually.
低频标签存储一个短 ID,只有几个字节长。标签的 ID 与存储在控制器或对讲机数据库中的 ID 进行比较。然而,一旦通电,该卡就会将其 ID 发送给任何询问的人。通常,ID 刻在卡本身上,因此您可以拍照并将其手动输入到 Flipper 中。

Popular 125 kHz protocols:
流行的 125 kHz 协议:
- EM-Marin — EM4100, EM4102. The most popular protocol in CIS. Can be read from about a meter because of its simplicity and stability.
EM-马林— EM4100、EM4102。 CIS 中最流行的协议。由于其简单性和稳定性,可以读取大约一米的读数。 - HID Prox II — low-frequency protocol introduced by HID Global. This protocol is more popular in the western countries. It is more complex and the cards and readers for this protocol are relatively expensive.
HID Prox II — HID Global 推出的低频协议。该协议在西方国家更为流行。它比较复杂,并且该协议的卡和读卡器相对昂贵。 - Indala — very old low-frequency protocol that was introduced by Motorola, and later acquired by HID. You are less likely to encounter it in the wild compared to the previous two because it is falling out of use.
Indala — 非常古老的低频协议,由 Motorola 推出,后来被 HID 收购。与前两者相比,你在野外遇到它的可能性较小,因为它已经不再使用了。
In reality, there are a lot more low-frequency protocols. But they all use the same modulation on the physical layer and may be considered, in one way or another, a variation of those listed above. At the time of writing Flipper can read, save, emulate and write all three protocols. There may be other ones, which are not supported in Flipper's firmware, but as the 125 kHz subsystem is implemented programmatically, we can add them in the future.
事实上,低频协议还有很多。但它们都在物理层上使用相同的调制,并且可以以某种方式被视为上面列出的那些的变体。在撰写本文时,Flipper 可以读取、保存、模拟和写入所有三种协议。可能还有其他的,Flipper 的固件不支持,但由于 125 kHz 子系统是通过编程实现的,我们可以在将来添加它们。
EM-Marin EM-马林
[Video] Flipper reading an EM-Marin tag
[视频] Flipper 读取 EM-Marin 标签
EM-Marin is the most common format we have in CIS. It is simple and has no copy-protection. EM-Marin cards usually have EM4100 chips inside, but there are others as well. For example, you can have an EM4305 which can be re-written unlike the EM4100.
EM-Marin 是 CIS 中最常见的格式。它很简单并且没有复制保护。 EM-Marin 卡通常内置 EM4100 芯片,但也有其他芯片。例如,您可以拥有可重写的 EM4305,这与 EM4100 不同。
To read a low-frequency card go into the Flipper menu 125 kHz RFID —> Read and place the tag on the back of the device. Flipper will attempt to determine the protocol and on success will display it alongside the card's ID. Since Flipper is trying all the protocols in one go it takes a bit of time. For example, you will need a couple of seconds to read an Indala card.
要读取低频卡,请进入 Flipper 菜单125 kHz RFID —> Read标签并将其放置在设备背面。 Flipper 将尝试确定协议,成功后会将其显示在卡的 ID 旁边。由于 Flipper 一次性尝试所有协议,因此需要一些时间。例如,您需要几秒钟才能读取 Indala 卡。

卡上和脚蹼上有唯一的 EM-Marin ID
EM4100's unique code is 5 bytes long. Sometimes you can find it on the card itself. The unique code may be written both as a decimal or in hex. Flipper displays the code in hex, however, EM-Marin cards usually just have the 3 lower bytes written on them, and not the full 5-byte number. If there is no way to read them from the card, the other 2 bytes can be brute-forced.
EM4100 的唯一代码长度为 5 个字节。有时您可以在卡上找到它。唯一代码可以写为十进制或十六进制。 Flipper 以十六进制显示代码,但是,EM-Marin 卡通常只写有 3 个较低字节,而不是完整的 5 字节数字。如果无法从卡中读取它们,则可以暴力破解其他 2 个字节。[Video] Emulating 125 kHz RFID to open an electric door lock
[视频]模拟125kHz RFID打开电动门锁
To emulate an RFID tag we need to go into the menu 125 kHz RFID —> Saved, choose the necessary tag and then press Emulate.
要模拟 RFID 标签,我们需要进入菜单125 kHz RFID —> Saved ,选择必要的标签,然后按Emulate 。
Some intercoms try to protect themselves from key duplication by sending a write command prior to reading. If the write succeeds, that tag is considered fake. When Flipper emulates RFID there is no way for the reader to distinguish it from the original one, so no such problems occur.
一些对讲机试图通过在读取之前发送写入命令来保护自己免受密钥重复。如果写入成功,则该标签被认为是假的。当Flipper模拟RFID时,阅读器无法将其与原始RFID区分开来,因此不会出现此类问题。
HID Prox HID 接近器
[Video] Flipper reading a HID26 tag
[视频] Flipper 读取 HID26 标签
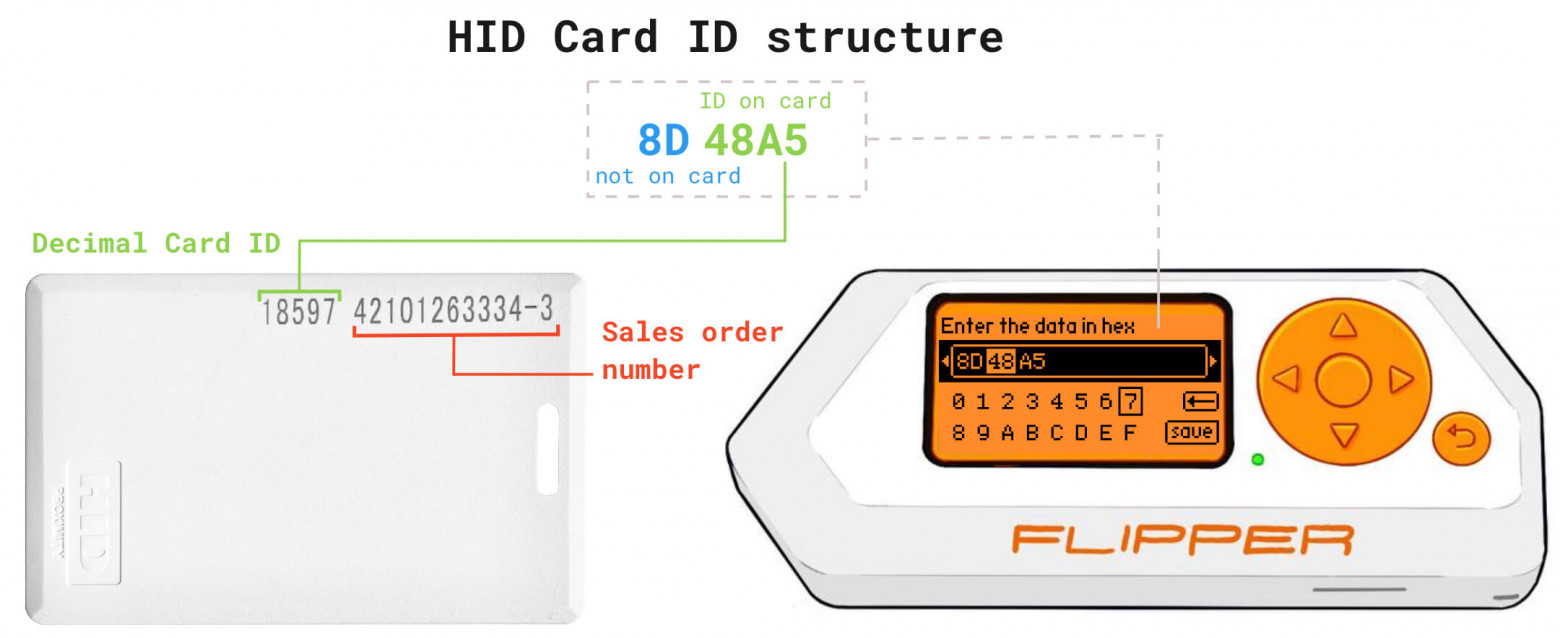
HID Global — is the largest manufacturer of RFID devices in the world. They have several high and low-frequency RFID protocols. The most popular low-frequency HID protocol is the 26-bit H10301 (also known as HID26 or HID PROX II). The unique code is 3 bytes (24 bits) long, and 2 more bits are used for parity check (to ensure the integrity of data).
HID Global — 是世界上最大的 RFID 设备制造商。他们有多种高频和低频 RFID 协议。最流行的低频 HID 协议是 26 位 H10301(也称为 HID26 或 HID PROX II)。唯一码长3个字节(24位),另外2位用于奇偶校验(以确保数据的完整性)。
Some HID26 cards have numbers written on them - they are the sales order number and the card's ID. You can't figure out the whole 3 bytes with that information alone, the card only has the 2 bytes printed on it in decimal format. That is the card's ID.
某些 HID26 卡上写有数字 - 它们是销售订单号和卡的 ID。仅凭该信息无法算出全部 3 个字节,卡片上仅以十进制格式印有 2 个字节。那就是卡的 ID。
卡上的 HID26 数据结构以及使用 Flipper 读取时的数据结构
Flipper can only work with the HID26 protocol of the HID family. In the future, we plan to extend this list. HID26 is the most popular one since it is compatible with most digital access control systems.
Flipper 只能与 HID 系列的 HID26 协议配合使用。将来,我们计划扩展此列表。 HID26 是最受欢迎的一种,因为它与大多数数字访问控制系统兼容。[Video] Flipper emulating a low-frequency card and opening the turnstile
【视频】Flipper模拟低频卡并打开闸机
Indala 因达拉
Indala is an RFID protocol developed by Motorola and later acquired by HID. It's a very old protocol that you won't find in modern access control systems. Rare as it is, you may sometimes find it in the field. At the time of writing Flipper works with Indala I40134.
Indala 是由 Motorola 开发的 RFID 协议,后来被 HID 收购。这是一个非常古老的协议,在现代访问控制系统中找不到。尽管很罕见,但有时您可能会在野外发现它。在撰写本文时,Flipper 使用 Indala I40134。[Video] Flipper reading an Indala card
[视频] Flipper 读 Indala 卡片
Same as with HID26, cards using Indala I40134 have a unique code that is 3 byte long. Unfortunately, Indala's data structure is proprietary and everyone who wishes to support this protocol is forced to choose whichever byte order they want, and also how they interpret the signal on the hardware level.
与 HID26 相同,使用 Indala I40134 的卡具有 3 字节长的唯一代码。不幸的是,Indala 的数据结构是专有的,每个希望支持该协议的人都被迫选择他们想要的字节顺序,以及他们如何在硬件级别解释信号。
All these protocols are so simple that the card's ID may be entered manually without the original card. Having your card's ID in text format, anyone owning a Flipper could enter it manually.
所有这些协议都非常简单,无需原始卡即可手动输入卡的 ID。有了文本格式的卡 ID,任何拥有 Flipper 的人都可以手动输入它。
Manually Entering the Card's ID
手动输入卡的 ID
[Video] Entering an Indala card's ID without having the card itself
[视频] 在没有卡本身的情况下输入 Indala 卡的 ID
To add the card's ID go to the menu and choose 125 kHz RFID —> Add manually, then the protocol and enter the ID. The card added will be saved to the SD-card, and may then be emulated or written to a blank.
要添加卡的 ID,请进入菜单并选择125 kHz RFID —> Add manually ,然后选择协议并输入 ID。添加的卡将保存到 SD 卡,然后可以进行模拟或写入空白。
Writing to a Blank Card
写入空白卡
There are special blank cards that support any of the three protocols mentioned above (EM-Marin, HID Prox, Indala). T5577 is the most popular blank card type. To write an ID to a blank card go to the menu 125 kHz RFID —> Saved, then choose the key you want and press Write.
有一些特殊的空白卡支持上述三种协议中的任何一种(EM-Marin、HID Prox、Indala)。 T5577 是最流行的空白卡类型。要将 ID 写入空白卡,请转至菜单125 kHz RFID —> Saved ,然后选择所需的密钥并按Write 。[Video] Writing to a T5577 blank card
[视频]写入T5577空白卡
High-Frequency 13.56 MHz Protocols
高频 13.56 MHz 协议

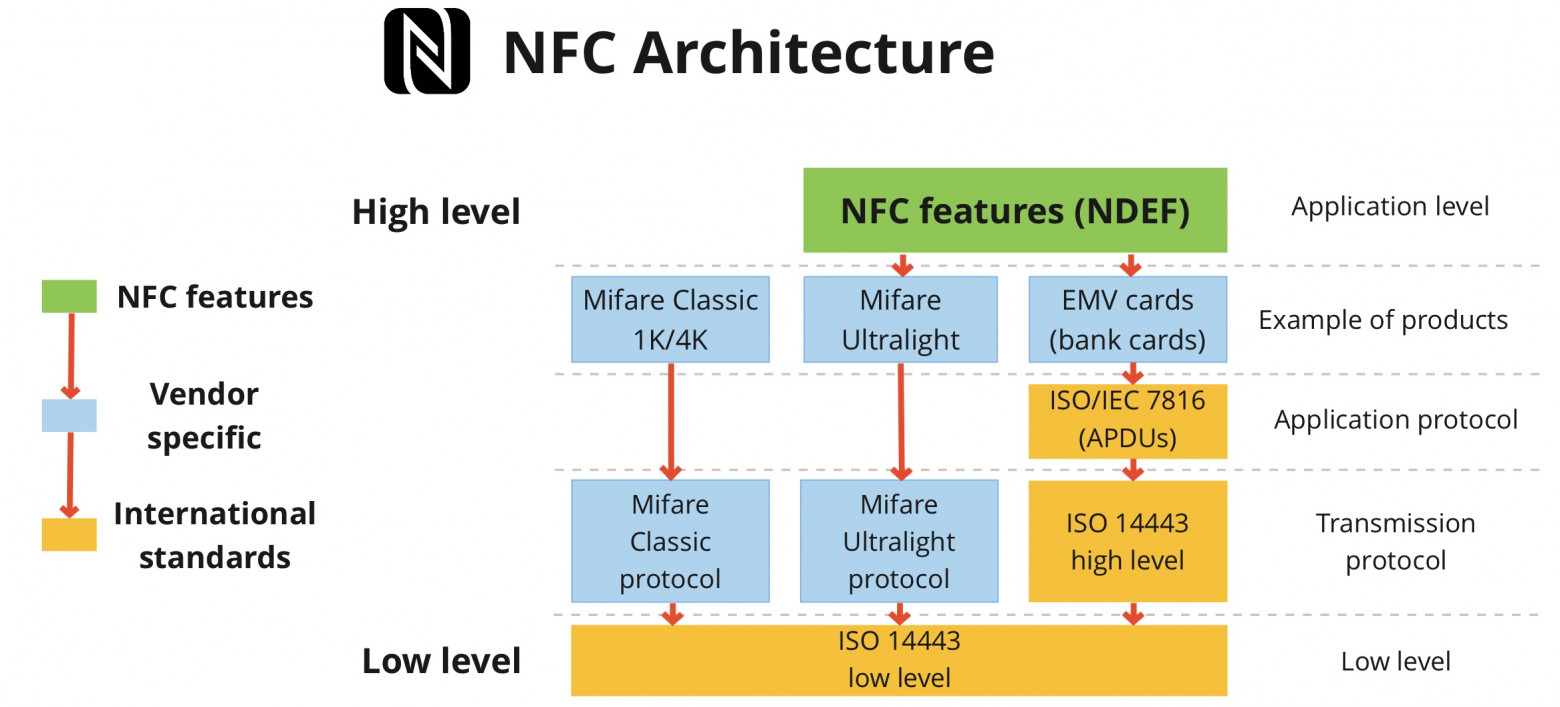
High-frequency 13.56 MHz tags are a set of standards and protocols. They are usually referred to as NFC, but that's not always correct. The basic protocol set used on the physical and logical levels is ISO 14443. High-level protocols, as well as alternative standards (like ISO 19092), are based upon it.
高频 13.56 MHz 标签是一组标准和协议。它们通常被称为NFC ,但这并不总是正确的。物理和逻辑级别上使用的基本协议集是 ISO 14443。高级协议以及替代标准(如 ISO 19092)均基于它。
ISO 14443-A seems to be the most common implementation. Almost all of the public transport and office passes use it, and it's used in bank cards as well.
ISO 14443-A似乎是最常见的实施方式。几乎所有的公共交通和办公通行证都使用它,银行卡也使用它。
NFC 的架构得到简化
To put it simply, NFC's architecture works like this: the transmission protocol is chosen by the company making the cards and implemented based on the low-level ISO 14443. For example, NXP invented its own high-level transmission protocol called Mifare. But on the lower level, Mifare cards are based on ISO 14443-A standard.
简单来说,NFC的架构是这样的:传输协议由制造卡的公司选择,并基于低级ISO 14443实现。例如,NXP发明了自己的高级传输协议,称为Mifare。但在较低层面上,Mifare 卡基于 ISO 14443-A 标准。
Flipper can interact with both the low-level ISO 14443 protocol, as well as Mifare Ultralight data transfer protocol and EMV used in bank cards. We're working on adding support for Mifare Classic and NFC NDEF. A thorough look at the protocols and standards that make up NFC is worth a separate article which we plan to have up later.
Flipper 可以与低级 ISO 14443 协议以及银行卡中使用的 Mifare Ultralight 数据传输协议和 EMV 进行交互。我们正在努力添加对 Mifare Classic 和 NFC NDEF 的支持。全面了解构成 NFC 的协议和标准值得单独撰写一篇文章,我们计划稍后发布。
Plain UID of the ISO 14443-A Standard
ISO 14443-A 标准的普通 UID
[Video] Reading a UID from a High-frequency tag of an unknown type
[视频]从未知类型的高频标签中读取UID
All high-frequency cards based on ISO 14443-A standard have a unique chip ID. It acts as the card's serial number, like a network card's MAC address. Usually, the UID is 4 or 7 bytes long, but can rarely go up to 10. UIDs are not a secret and they are easily readable, sometimes even printed on the card itself.
所有基于 ISO 14443-A 标准的高频卡都具有唯一的芯片 ID。它充当卡的序列号,就像网卡的 MAC 地址一样。通常,UID 的长度为 4 或 7 个字节,但很少会达到 10 个字节。UID 不是秘密,它们很容易读取,有时甚至打印在卡本身上。
There are many access control systems that rely on UID to authenticate and grant access. Sometimes this happens even when RFID tags support cryptography. Such misuse brings them down to the level of the dumb 125 kHz cards in terms of security. Virtual cards (like Apple Pay) use a dynamic UID so that phone owners won't go opening doors with their payment app.
有许多访问控制系统依赖 UID 来验证和授予访问权限。有时,即使 RFID 标签支持加密,也会发生这种情况。这种误用使它们在安全性方面下降到愚蠢的 125 kHz 卡的水平。虚拟卡(如 Apple Pay)使用动态 UID,这样手机所有者就不会使用他们的支付应用程序开门。[Video] iPhone generates a new UID for each time Apple Pay is read
[视频] iPhone 每次读取 Apple Pay 时都会生成一个新的 UID
Since UID is a low-level attribute, you might find yourself in a situation when UID is already read, but the high-level data transfer protocol is still unknown. You can read, emulate and manually input UID using Flipper for the primitive readers that use UID for authorization.
由于 UID 是低级属性,因此您可能会发现自己处于 UID 已被读取但高级数据传输协议仍然未知的情况。对于使用UID进行授权的原始阅读器,您可以使用Flipper来读取、模拟和手动输入UID。
Reading the UID VS Reading the Data Inside
读取UID VS 读取里面的数据
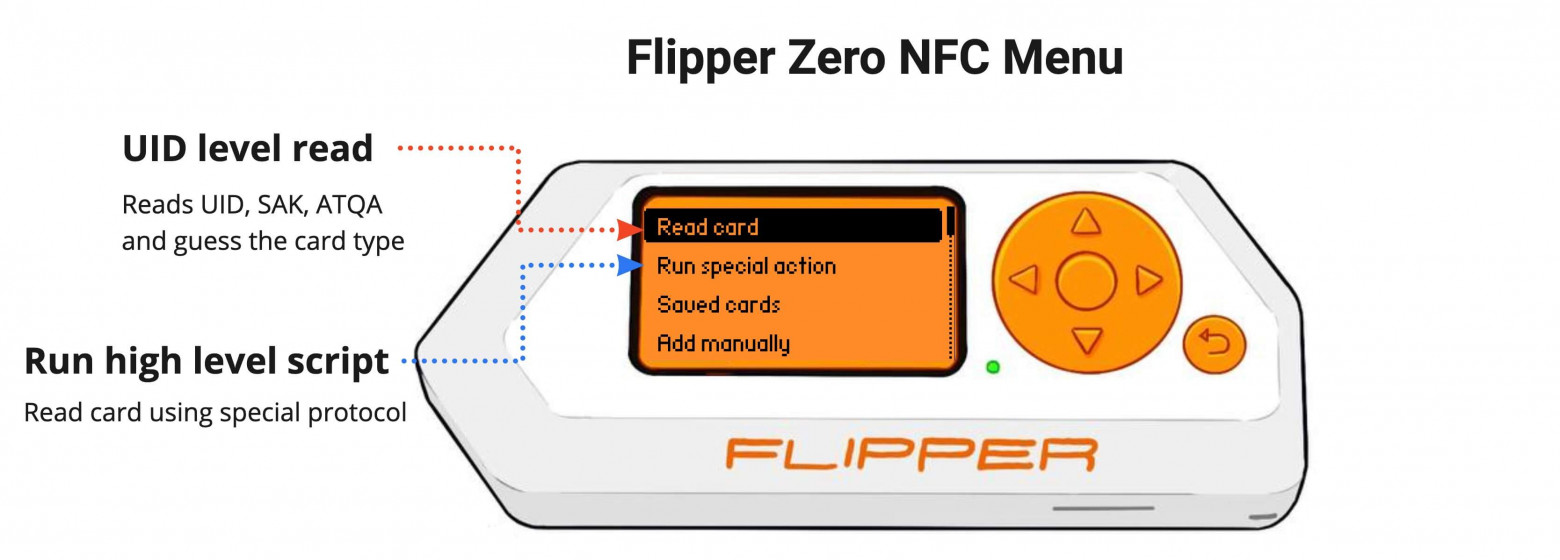
NFC读取菜单分为低级读取和高级读取两部分
In Flipper, reading 13.56 MHz tags can be divided into two parts:
在Flipper中,读取13.56 MHz标签可以分为两部分:
- Low-level read — reads only the UID, SAK, and ATQA. Flipper tries to guess the high-level protocol based on this data read from the card. You can't be 100% certain with this, as it is just an assumption based on certain factors.
低级读取— 仅读取 UID、SAK 和 ATQA。 Flipper 尝试根据从卡读取的数据来猜测高级协议。您不能 100% 确定这一点,因为它只是基于某些因素的假设。 - High-level read — reads the data from the card's memory using a specific high-level protocol. That would be reading the data on a Mifare Ultralight, reading the sectors from a Mifare Classic, or reading the card's attributes from PayPass/Apple Pay.
高级读取— 使用特定的高级协议从卡的内存中读取数据。这将是读取 Mifare Ultralight 上的数据、读取 Mifare Classic 上的扇区或从 PayPass/Apple Pay 上读取卡的属性。
To use a specific high-level protocol when reading data go to NFC —> Run special action and choose the type of tag you want to read.
要在读取数据时使用特定的高级协议,请转至NFC —> Run special action并选择您要读取的标签类型。
To try and guess the type of tag and to read the UID go to NFC -> Read card. So far Flipper can only detect Mifare Ultralight and EMV bank card.
要尝试猜测标签类型并读取 UID,请转至NFC -> Read card 。目前Flipper只能检测Mifare Ultralight和EMV银行卡。
Mifare Ultralight Mifare 超轻
[Video] Reading data off a Mifare Ultralight
[视频] 从 Mifare Ultralight 读取数据
Mifare is a family of contactless smart cards with several high-level protocols. The simplest of those is Mifare Ultralight. In its basic version, it has only 64 bytes of embedded flash memory and no cryptographic protection. Flipper can both read and emulate Mifare Ultralight cards. Such tags are often used as passes granting access to offices, houses and public transport. Moscow public transport tickets for example are using Mifare Ultralight.
Mifare 是一个非接触式智能卡系列,具有多种高级协议。其中最简单的是 Mifare Ultralight。在其基本版本中,它只有 64 字节的嵌入式闪存,并且没有加密保护。 Flipper 可以读取和模拟 Mifare Ultralight 卡。此类标签通常用作进入办公室、房屋和公共交通的通行证。例如,莫斯科公共交通票就使用 Mifare Ultralight。
EMV Bank Cards (PayPass, payWave, Apple Pay, Google Pay)
EMV 银行卡(PayPass、payWave、Apple Pay、Google Pay)
[Video] Reading data from a bank card
[视频]读取银行卡数据
EMV (Europay, Mastercard, and Visa) — is the international standard set for bank cards. Bank cards now are full-fledged smart cards with complex data exchange protocols and support for asymmetric encryption. Apart from simply reading the UID, you can extract a lot more data from a bank card. It's possible to get the full card number (the 16 digits on the front of the card), validity date, and in some cases even the owner's name along with a list of the most recent transactions.
EMV(Europay、Mastercard 和 Visa)——是为银行卡制定的国际标准。银行卡现在已经是成熟的智能卡,具有复杂的数据交换协议并支持非对称加密。除了简单地读取UID之外,您还可以从银行卡中提取更多数据。可以获得完整的卡号(卡正面的 16 位数字)、有效日期,在某些情况下甚至可以获得所有者的姓名以及最近交易的列表。
Since the EMV standard might be implemented differently, the data that can be extracted may vary from card to card. You can't read the CVV this way (the 3 digits on the back of the card).
由于 EMV 标准的实施方式可能不同,因此可提取的数据可能因卡而异。您无法通过这种方式读取 CVV(卡背面的 3 位数字)。
Bank cards are protected from replay attacks, so copying it with Flipper and then trying to emulate it to pay for something won't work.
银行卡受到重放攻击的保护,因此用 Flipper 复制它,然后尝试模仿它来支付某些东西是行不通的。
Tokenized Apple Pay Card VS Physical Bank Card
代币化 Apple Pay 卡 VS 实体银行卡
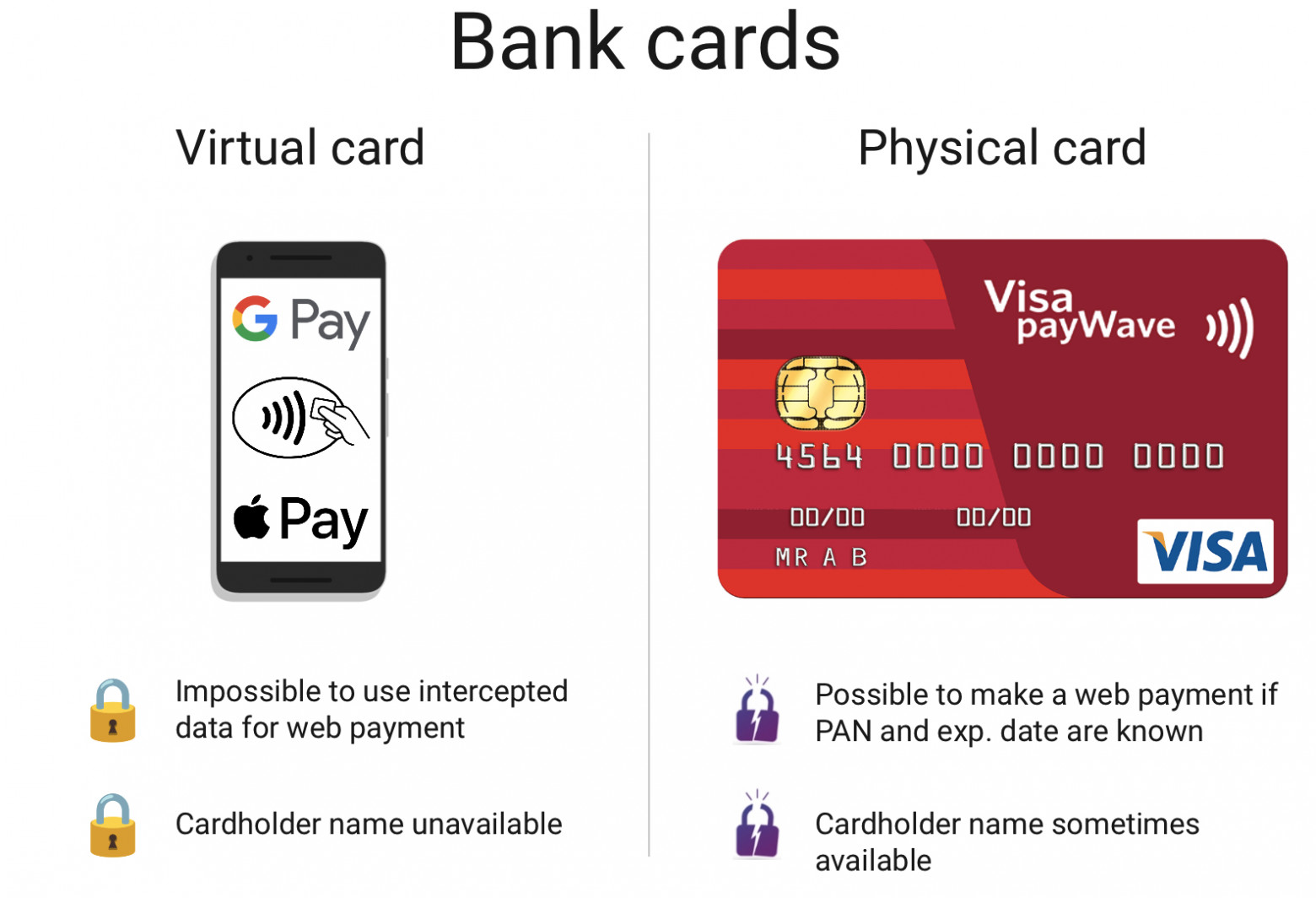
虚拟银行卡与实体银行卡的安全性比较
Compared to a plastic bank card, the virtual card you have in your phone provides less information and is safer for offline payments.
与塑料银行卡相比,手机中的虚拟卡提供的信息更少,线下支付更安全。
Apple Pay and Google Pay have several advantages:
Apple Pay 和 Google Pay 有几个优点:
- They don't allow using captured data for online payments – a normal card can be used for Card-Not-Present transactions (CNP), you can sometimes pay online or on the phone. Intercepted virtual card data can't be used in this manner. After registering a card with Apple Pay all payments go through the virtual token and all operations are cryptographically signed. Reading Apple Pay data results in a PAN and an expiration date of the virtual token, not the original physical card. Thus if someone tries to use the data intercepted from a virtual card to pay online such payment will be declined without a specific signature.
他们不允许使用捕获的数据进行在线支付- 普通卡可用于无卡交易 (CNP),您有时可以在线或通过电话支付。截获的虚拟卡数据不能以这种方式使用。在 Apple Pay 上注册卡后,所有支付都会通过虚拟令牌进行,并且所有操作都会经过加密签名。读取 Apple Pay 数据会生成 PAN 和虚拟令牌(而不是原始物理卡)的到期日期。因此,如果有人试图使用从虚拟卡截取的数据进行在线支付,则在没有特定签名的情况下,此类支付将被拒绝。 - They don't disclose the card owner's name — some contactless cards can transfer the cardholder name and recent transactions data. Virtual cards don't do that.
他们不会透露持卡人的姓名- 一些非接触式卡可以传输持卡人姓名和最近的交易数据。虚拟卡则不能做到这一点。
Bank card support in Flipper is implemented solely for high-level protocol demonstration purposes only. We do not plan to extend this function further. Contactless bank cards security is good enough not to worry that devices such as Flipper can be used to attack bank cards.Flipper 中的银行卡支持仅出于高级协议演示目的而实现。我们不打算进一步扩展此功能。非接触式银行卡安全性足够好,不用担心Flipper等设备可以用来攻击银行卡。


发表回复